DoH in Microsoft Windows OS
Until this moment Microsoft Windows OS doesn’t support DNS over HTTPS, The feature will most likely be implemented in future builds but no body knows when is that however, You can still take a peak into the feature which is in preview mode/
Benefit of using DoH on an OS level
The benefit of using DoH on an Operating System level would provide more certainty that your DNS queries leave your computer without being read by any other party even if that is your ISP.
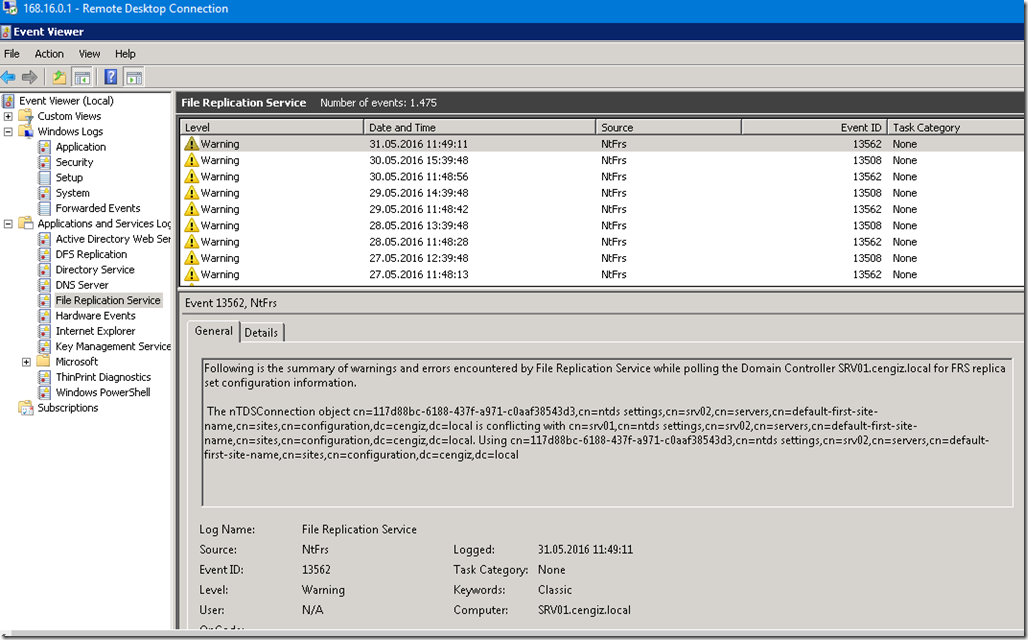
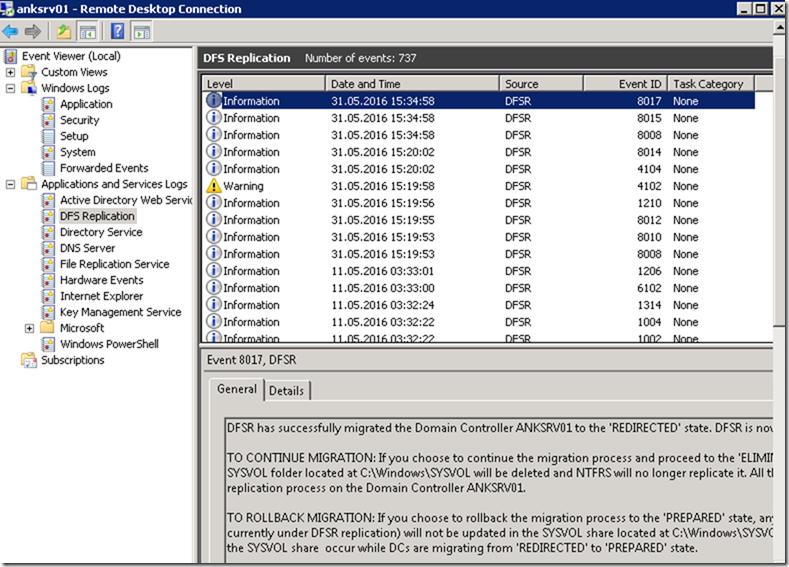
A simple DNS nslookup query using Wireshark on your computer would show you how serious this topic is. After installing Wireshark you’ll be able to see that all of your dns queries are in clear text and can be read by anyone until it gets to the destination website/server.
Demonstration of DNS lookup without DoH
After installing Wireshark, I fire up Powershell or CMD and try to nslookup google.com and it’ll show what I just queried for.
So how to make sure that your DNS queries don’t leave your computer in clear text format? and since Microsoft OS is not DoH ready yet what can you do?
In my case, I am already using encrypted DNS on firewall level as I have Pfsense acting as a router and it already supports DoH but still not pretty satisfied :).
DNSCrypt as a solution
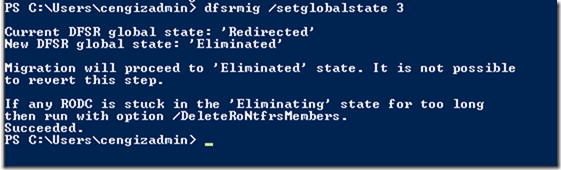
Since the foundation of DoH I have been looking for a solution that would work on Microsoft Windows OS and luckily someone already created this great project called Simple DNSCrypt which not just enables the encryption of DNS queries on your OS but also enables this to work as a service.
Installing DNSCrypt would create a Windows based Service which would start automatically when your OS boots and logs into Windows.
The service is called DNSCrypt Client Proxy
Add alt text
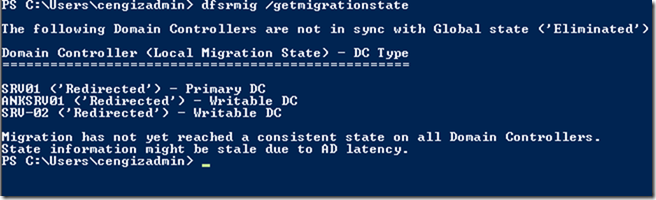
DNSCrypt has a simple interface, You can pick up the DNS Server where to forward queries to and it works with proof.
Right after the installation of this tiny app, launch it as an administrator and configure it as in the below screenshot. You can choose to install the service or not.
Add alt text
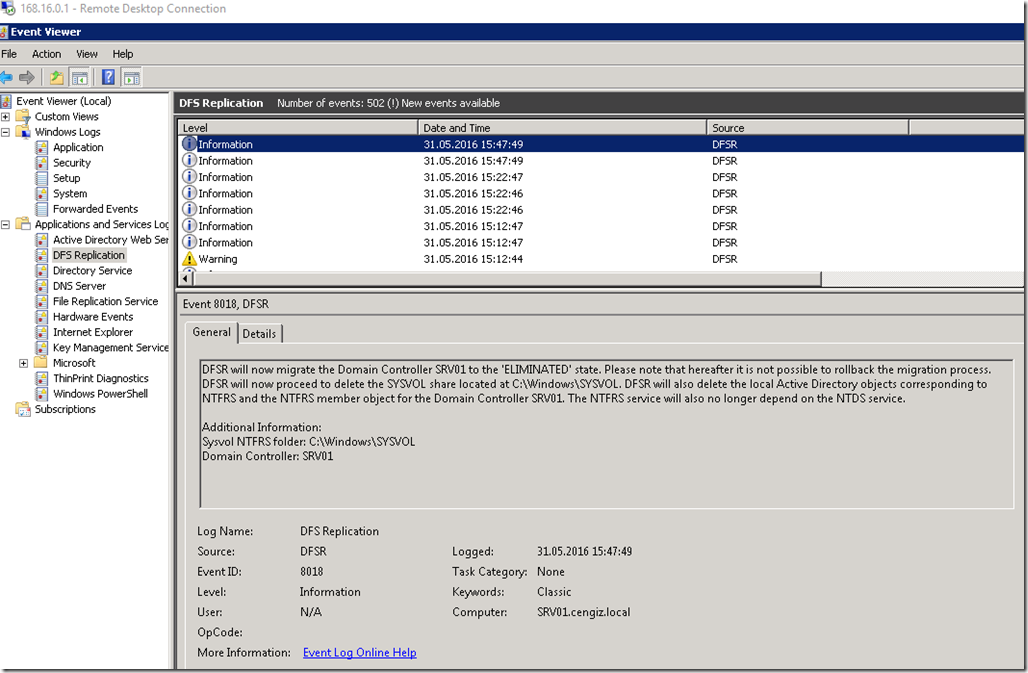
Right after you enable it (By clicking on your Network Card box) that will start protecting your DNS queries. Let’s go ahead with a little demo
I am going to start Wireshark after enabling DnsCrypt and do a google dns lookup , As you can see below on wireshark it’s not returning any dns queries.
When you install Simple DNSCrypt it changes your Preferred DNS configuration to localhost so that all queries is passed through the app in DNS over HTTPS which doesn’t allow even Wireshark to see it as DNS.
So that makes it pretty secure and not even your firewall will see it.
If you have any question please don’t hesitate to ask me
Official DNScrypt website https://simplednscrypt.org/
Support the project founder https://github.com/bitbeans/SimpleDnsCrypt
![clip_image001[4] clip_image001[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0014_thumb.png)
![clip_image002[4] clip_image002[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0024_thumb.png)
![clip_image003[4] clip_image003[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0034_thumb.png)
![clip_image004[4] clip_image004[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0044_thumb.png)
![clip_image005[4] clip_image005[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0054_thumb.png)
![clip_image006[4] clip_image006[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0064_thumb.png)
![clip_image007[4] clip_image007[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0074_thumb.png)
![clip_image008[4] clip_image008[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0084_thumb.png)
![clip_image009[4] clip_image009[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0094_thumb.png)
![clip_image010[4] clip_image010[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0104_thumb.png)
![clip_image011[4] clip_image011[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0114_thumb.png)
![clip_image012[4] clip_image012[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0124_thumb.png)
![clip_image013[4] clip_image013[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0134_thumb.png)
![clip_image014[4] clip_image014[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0144_thumb.png)
![clip_image015[4] clip_image015[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0154_thumb.png)
![clip_image016[4] clip_image016[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0164_thumb.png)
![clip_image017[4] clip_image017[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0174_thumb.png)
![clip_image018[4] clip_image018[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0184_thumb.png)
![clip_image019[4] clip_image019[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0194_thumb.png)
![clip_image020[4] clip_image020[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0204_thumb.png)
![clip_image021[4] clip_image021[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0214_thumb.png)
![clip_image022[4] clip_image022[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0224_thumb.png)
![clip_image023[4] clip_image023[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0234_thumb.png)
![clip_image024[4] clip_image024[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0244_thumb.png)
![clip_image025[4] clip_image025[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0254_thumb.png)
![clip_image026[4] clip_image026[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0264_thumb.png)
![clip_image027[4] clip_image027[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0274_thumb.png)
![clip_image028[4] clip_image028[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0284_thumb.png)
![clip_image029[4] clip_image029[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0294_thumb.png)
![clip_image030[4] clip_image030[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0304_thumb.png)
![clip_image031[4] clip_image031[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0314_thumb.png)
![clip_image032[4] clip_image032[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0324_thumb.png)
![clip_image033[4] clip_image033[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0334_thumb.png)
![clip_image034[4] clip_image034[4]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0344_thumb.png)
![clip_image035[7] clip_image035[7]](https://www.moh10ly.com/wp-content/uploads/2019/11/clip_image0357_thumb.png)