Add-PSSnapin Microsoft.Exchange.Management.PowerShell.Snapin
Function Get-HiddenMailbox
{
[CmdletBinding()]
Param(
[Parameter(Mandatory=$True)][string]$Path,
[Parameter(Mandatory=$True)][string]$Database
)
<#Check for any remaining mailboxes in a database that you can’t delete.
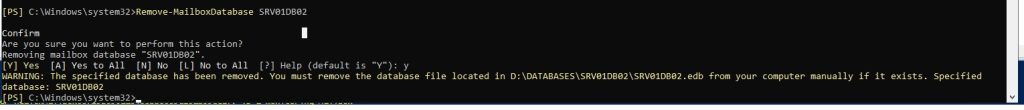
[PS] C:\Program Files\Microsoft\Exchange Server\V15\scripts>Remove-MailboxDatabase a-sb-com-udb1-v1
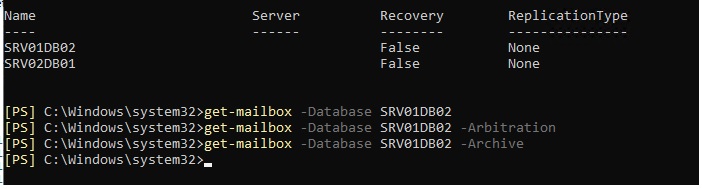
This mailbox database contains one or more mailboxes, mailbox plans, archive mailboxes, public folder mailboxes or
arbitration mailboxes, Audit mailboxes. To get a list of all mailboxes in this database, run the command Get-Mailbox
-Database <Database ID>. To get a list of all mailbox plans in this database, run the command Get-MailboxPlan. To get
a list of archive mailboxes in this database, run the command Get-Mailbox -Database <Database ID> -Archive. To get a
list of all public folder mailboxes in this database, run the command Get-Mailbox -Database <Database ID>
-PublicFolder. To get a list of all arbitration mailboxes in this database, run the command Get-Mailbox -Database
<Database ID> -Arbitration. To get a list of all Audit mailboxes in this database, run the command Get-Mailbox
-Database <Database ID> -AuditLog. To disable a non-arbitration mailbox so that you can delete the mailbox database,
run the command Disable-Mailbox <Mailbox ID>. To disable an archive mailbox so you can delete the mailbox database,
run the command Disable-Mailbox <Mailbox ID> -Archive. To disable a public folder mailbox so that you can delete the
mailbox database, run the command Disable-Mailbox <Mailbox ID> -PublicFolder. To disable a Audit mailbox so that you
can delete the mailbox database, run the command Get-Mailbox -AuditLog | Disable-Mailbox. Arbitration mailboxes should
be moved to another server; to do this, run the command New-MoveRequest <parameters>. If this is the last server in
the organization, run the command Disable-Mailbox <Mailbox ID> -Arbitration -DisableLastArbitrationMailboxAllowed to
disable the arbitration mailbox. Mailbox plans should be moved to another server; to do this, run the command
Set-MailboxPlan <MailboxPlan ID> -Database <Database ID>.
+ CategoryInfo : InvalidOperation: (a-sb-com-udb1-v1:DatabaseIdParameter) [Remove-MailboxDatabase], Assoc
iatedUserMailboxExistException
+ FullyQualifiedErrorId : [Server=SBG-MX03,RequestId=480ce97d-8492-41a9-82fa-93ed30efe652,TimeStamp=6/28/2022 9:04
:09 AM] [FailureCategory=Cmdlet-AssociatedUserMailboxExistException] 45D30D02,Microsoft.Exchange.Management.System
ConfigurationTasks.RemoveMailboxDatabase
+ PSComputerName : server.domain.local
#>
#Fist get DB’s HomeMDB value
#Write-host ‘Enter your Database Name’ -ForegroundColor Red -BackgroundColor Black
$DN = (Get-MailboxDatabase $Database).distinguishedName
$Date = (Get-date).ToString(“MM-dd-yyyy”)
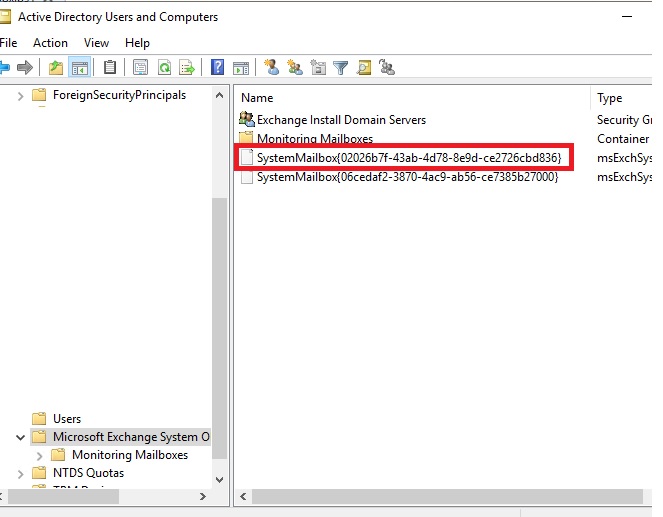
$Mailboxes = Get-ADObject -filter {(HomeMDB -eq $DN)}
$QueryResult = $Mailboxes.count
$CurrentCount = 0
foreach ($Mailbox in $Mailboxes){
try{
$ObjectProps = [Ordered]@{ ‘DisplayName’ = $Null; ‘UserPrincipalName’ = $Null; ‘Database’ = $Null; ‘Mailbox’ = $Null; ‘Arbitration’ = $Null; ‘Archive’ = $Null; ‘Audit’ = $Null; ‘Monitoring’ = $Null; ‘ErrorResponse’ = $Null}
$MBX = $Mailbox.name
$CurrentCount ++
Write-Progress -Activity “Checking Hidden Mailboxes in the database $DB $CurrentCount of $QueryResult “ -Status “Fetching $MBX“ -PercentComplete (($CurrentCount / $QueryResult) * 100)
$Result = New-Object -TypeName PSObject -Property $ObjectProps
$MailboxResult = Get-mailbox -Identity $MBX -ErrorAction SilentlyContinue
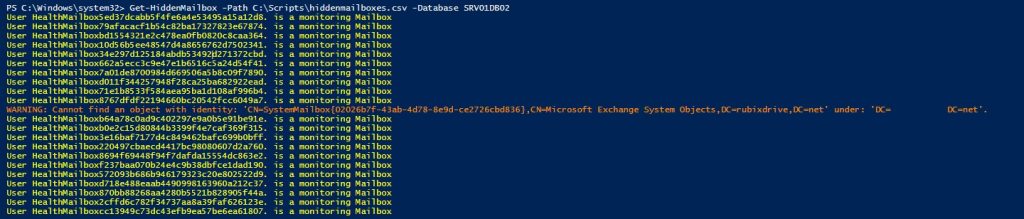
if ($MailboxResult){Write-Host “User $MBX. is a Mailbox” -ForegroundColor Green }
$ArbResult = get-mailbox -Identity $MBX -Arbitration -ErrorAction SilentlyContinue
if($ArbResult){Write-host “User $MBX. is an Arbitration Mailbox” -ForegroundColor White }
$ArchiveResult = get-mailbox -Identity $MBX -Archive -ErrorAction SilentlyContinue
if($ArchiveResult){Write-host “User $MBX. is a Archive” -ForegroundColor Red}
$AuditResult = get-mailbox -Identity $MBX -AuditLog -ErrorAction SilentlyContinue
if($AuditResult){Write-host “User $MBX. is a Audit Mailbox” -ForegroundColor DarkRed}
$Monitoring = get-mailbox -Identity $MBX -Monitoring -ErrorAction SilentlyContinue
if ($Monitoring){Write-host “User $MBX. is a monitoring Mailbox” -ForegroundColor Yellow }
$Result.DisplayName = $MBX
$Result.UserPrincipalName = (Get-ADUser -Identity $Mailbox.DistinguishedName).UserprincipalName
$Result.Database = $DB
$Result.Mailbox = $MailboxResult
$Result.Arbitration = $ArbResult
$Result.Archive = $ArchiveResult
$Result.Audit = $AuditResult
$Result.Monitoring = $Monitoring
$Result.ErrorResponse = ‘#N/A’
$NewPath = $path.Split(‘.’)[0] + ‘_’ + “$date“ + ‘.csv’
$Result | export-csv -path $NewPath -Delimiter ‘;’ -NoTypeInformation -NoClobber -Append -Encoding utf8
}
Catch{
Write-Warning $_.Exception.Message}
$Result | export-csv -path $NewPath -Delimiter ‘;’ -NoTypeInformation -NoClobber -Append -Encoding utf8
}
}