Installing Microsoft Azure Threat Protection (ATP) on Linux Devices
While playing with ATP on some windows devices, I was in the mood of trying the new Deepin 20 desktop flavor which is a famous Chinese Linux OS based system.
Microsoft doesn’t indicate anywhere that installation of ATP on a Linux client is possible but Linux server is mentioned in the official ATP installation documents.
How to Install?
After I installed the Deepin OS, I was really impressed by the new beautiful Linux design so I plan to use it and have it secure with ATP.
Prerequisites:
- Configure the Linux software repository for Ubuntu and Debian
- Application Installation
- Download the onboarding Package
- Client Config
1-Configure the Linux software repository for Ubuntu and Debian
You will need to install the required libraries, install Gpg, apt-transport-https and update repository metadata using the following commands one by one.
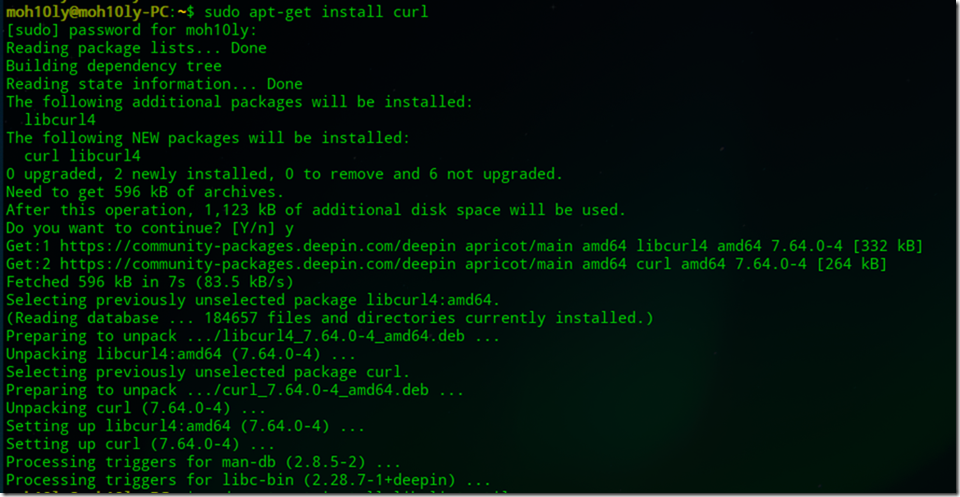
- sudo apt-get install curl
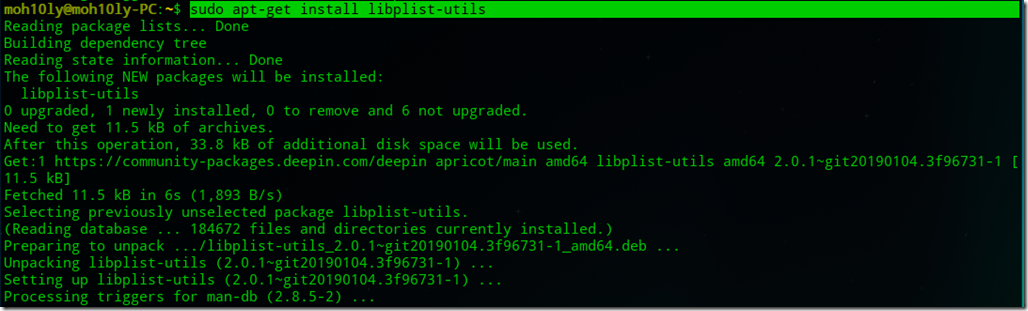
- sudo apt-get install libplist-utils
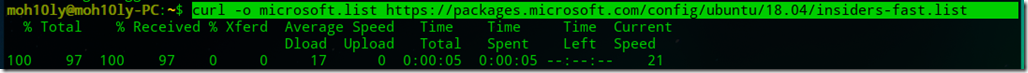
- curl -o microsoft.list https://packages.microsoft.com/config/ubuntu/18.04/insiders-fast.list
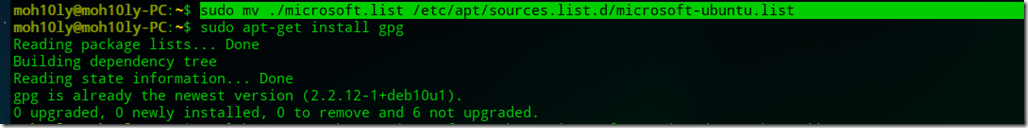
- sudo mv ./microsoft.list /etc/apt/sources.list.d/microsoft-ubuntu.list
- sudo apt-get install gpg
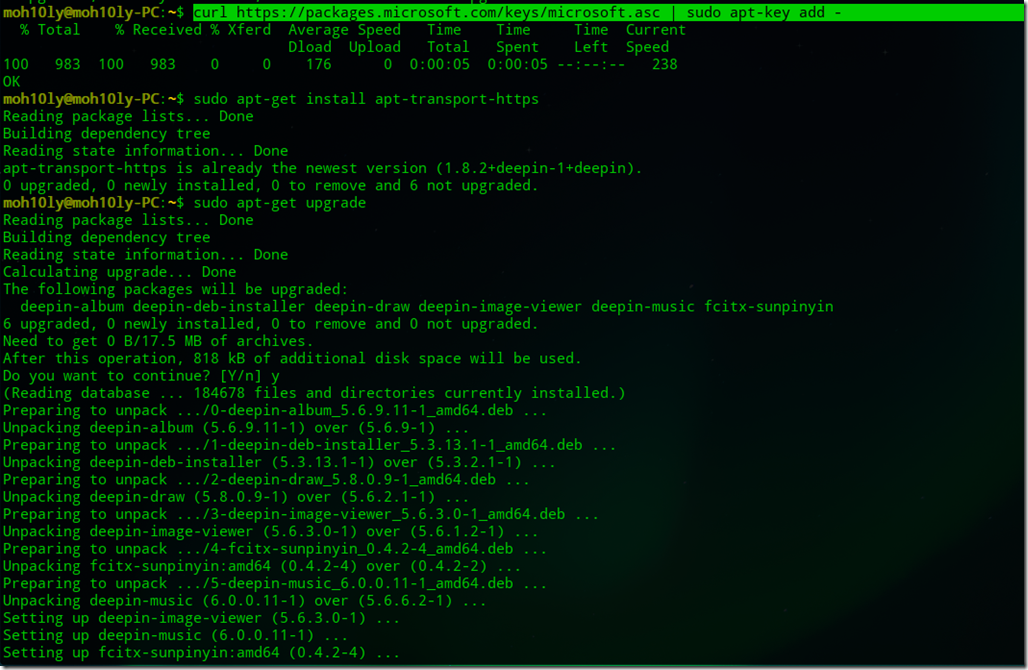
- curl https://packages.microsoft.com/keys/microsoft.asc | sudo apt-key add –
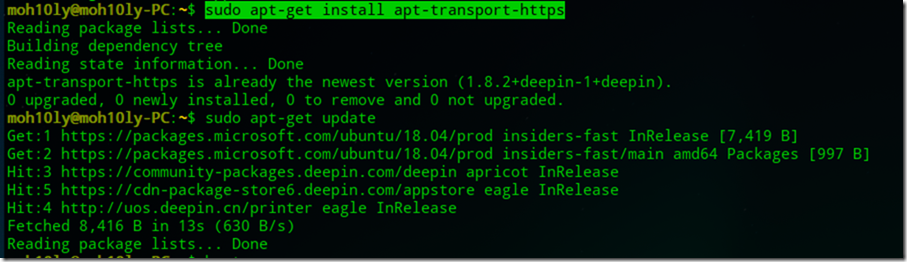
- sudo apt-get install apt-transport-https
- sudo apt-get update
After successfully installing all the libraries, I will go ahead and install the application
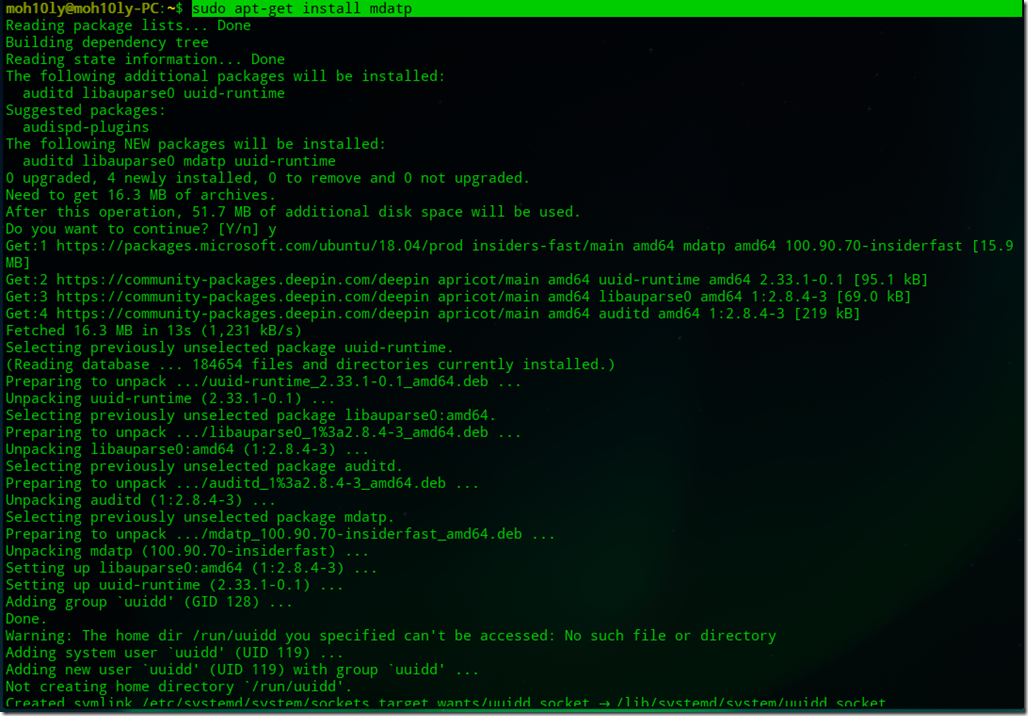
2- Application Installation
From the Linux client Terminal using sudo power user run the following script
sudo apt-get install mdatp
Once finished, You can go back to the ATP portal and download the Linux Onboarding package on the linux server/client you want to onboard
3- Download the onboarding Package
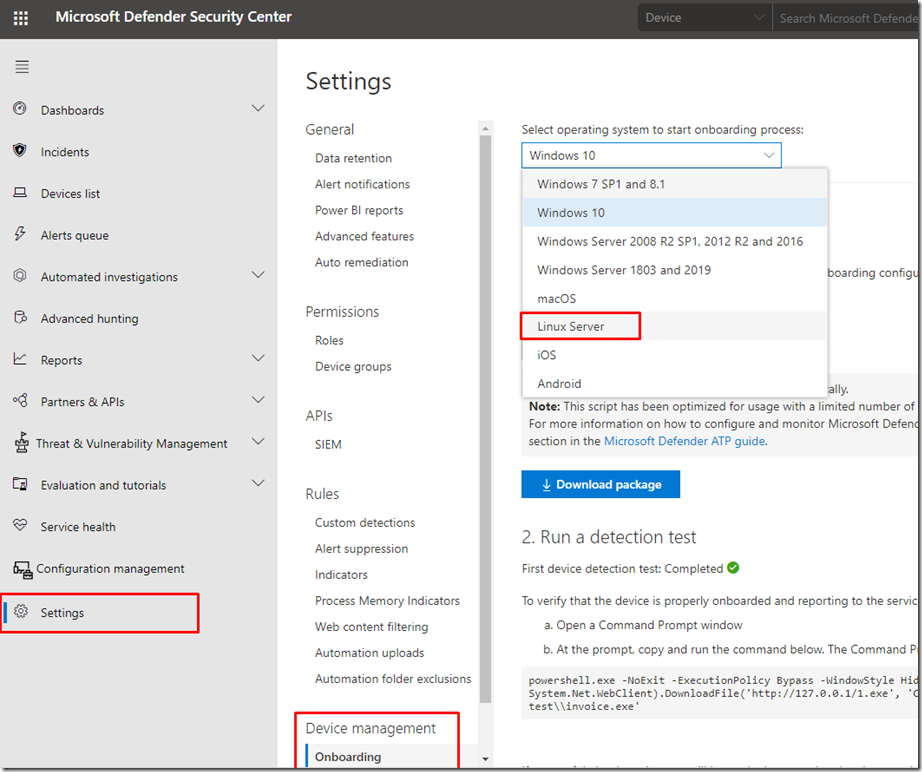
Since I am doing a single deployment not bulk, then I will go to the Microsoft Defender Security Center’s setting page and download the Linux package from the device management section.
The steps for the onboarding is already mentioned on that page so after you download the script you’ll know exactly what to do next.
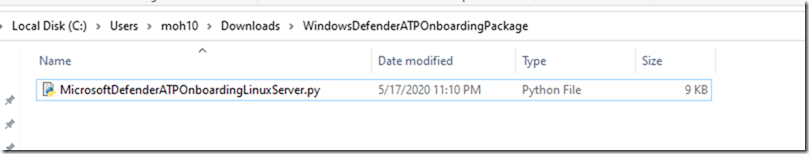
The file is 9kb python in size
Copy the file to your Linux Desktop
4- Client Config
From the terminal type in chmod a+x MicrosoftDefenderATPOnBoardingLinuxServer.py and hit enter
Note: python must be installed on this linux dervice.
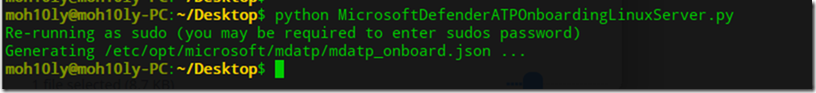
Then type python /MicrosoftDefenderATPOnBoardingLinuxServer.py
This will run pretty quick and will assign your Linux server/client with your Organization ID.
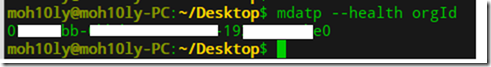
To see the Organization ID type:
mdatp –health orgId
Few minutes later you’ll be able to see the installation completion and the status through this command
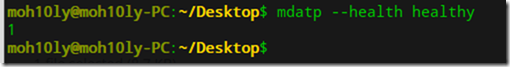
Check if WDATP is functioning as expected
mdatp –health healthy
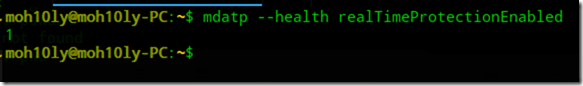
Check if WDATP agent is enabled
mdatp –health realTimeProtectionEnabled
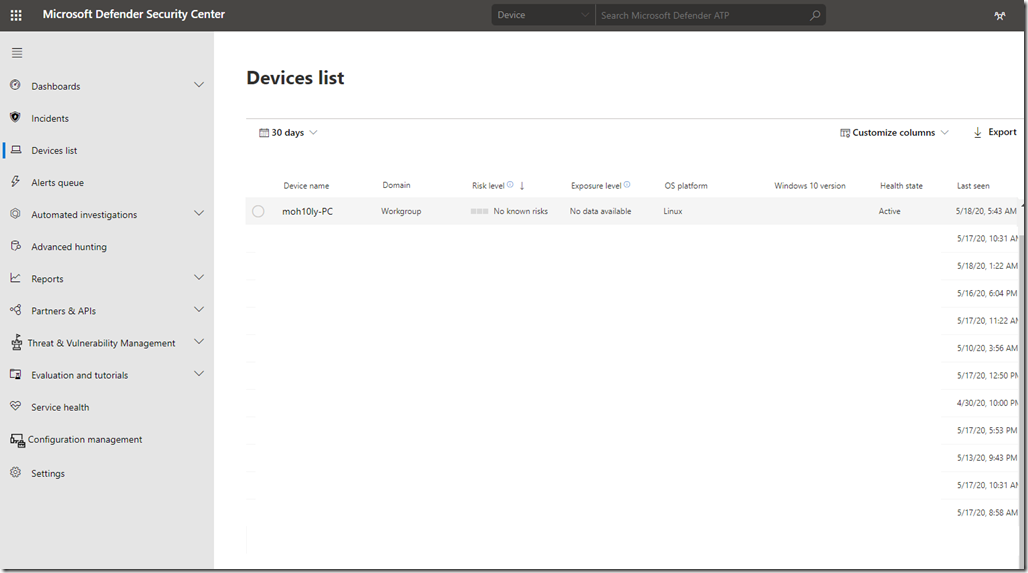
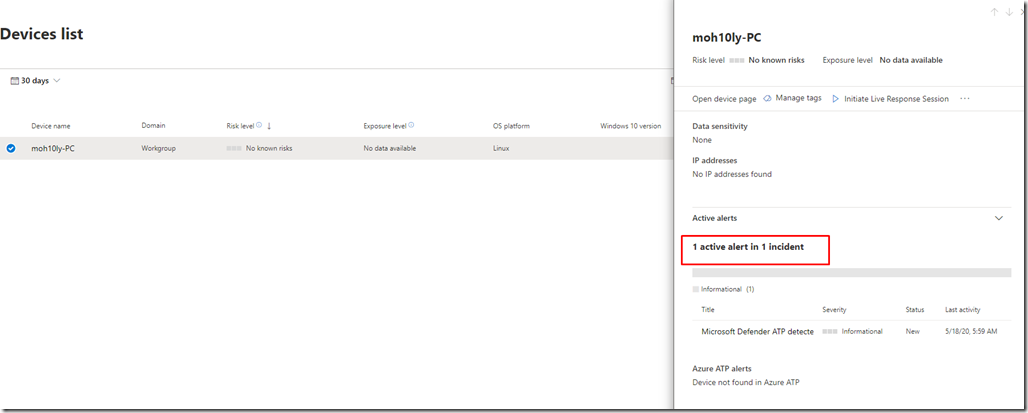
Let’s check on our ATP portal and see if the machine is showing there.
Note: It might take 5-15 mins to update the definitions of WDATP when onboarding.
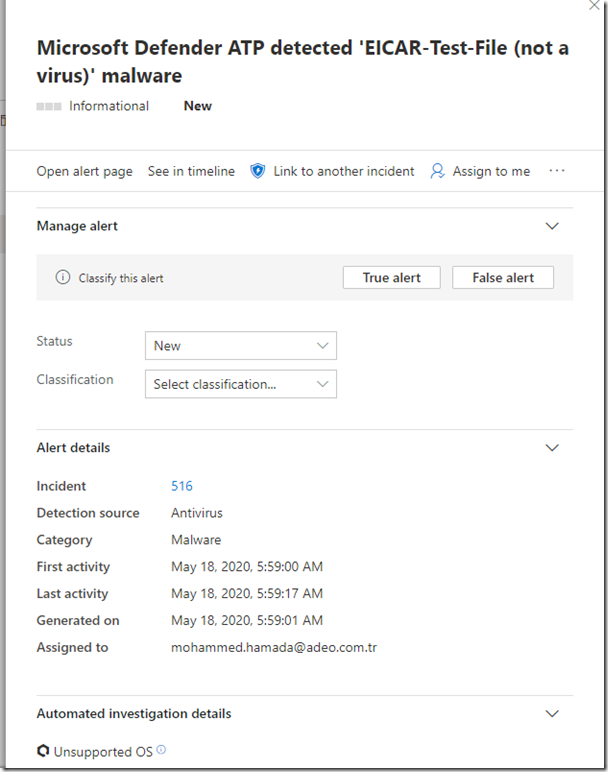
Running a detection Test:
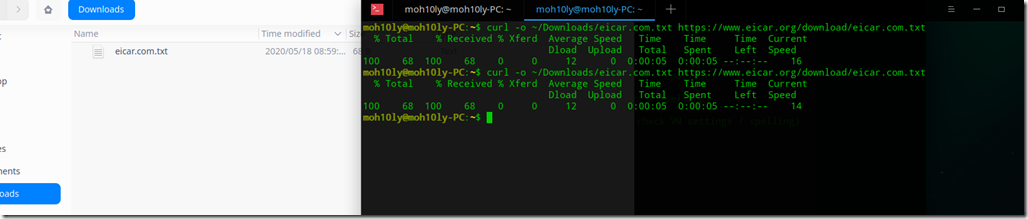
curl -o ~/Downloads/eicar.com.txt https://www.eicar.org/download/eicar.com.txt
In few seconds the file has disappeared
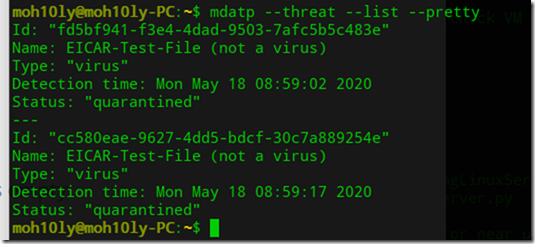
Checking for threats
mdatp –threat –list –pretty
Let’s see this on the ATP Portal
This is just a test malware not a real one therefore it wont harm your machine at all.
Hope this helps you with your deployments
Ref:
Deepin 20 Beta version
https://www.deepin.org/en/2020/04/15/deepin-20-beta/