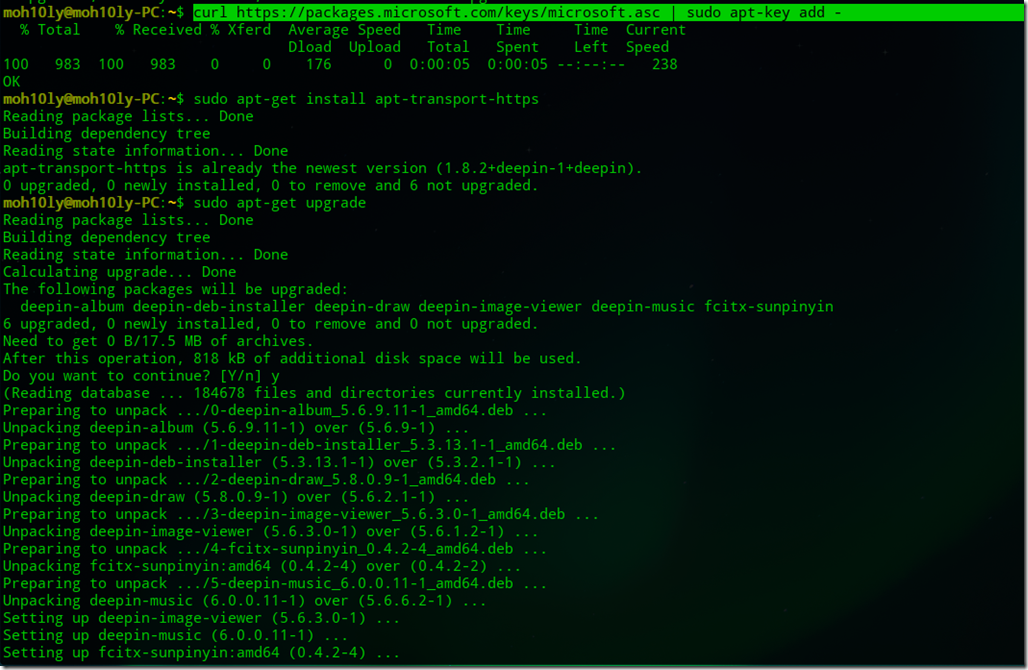
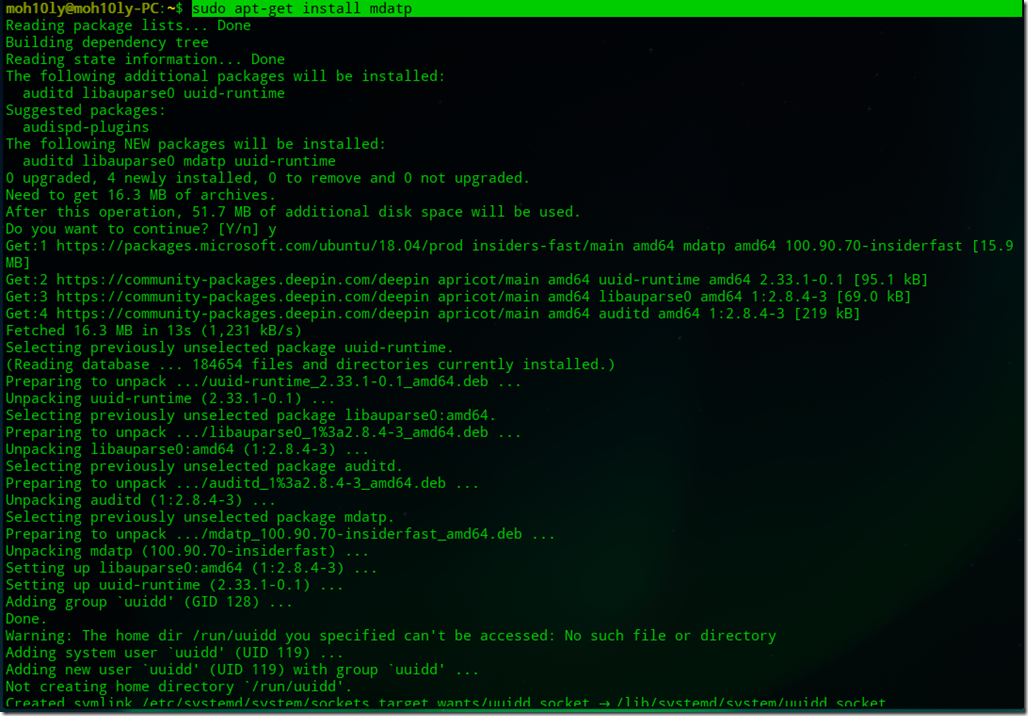
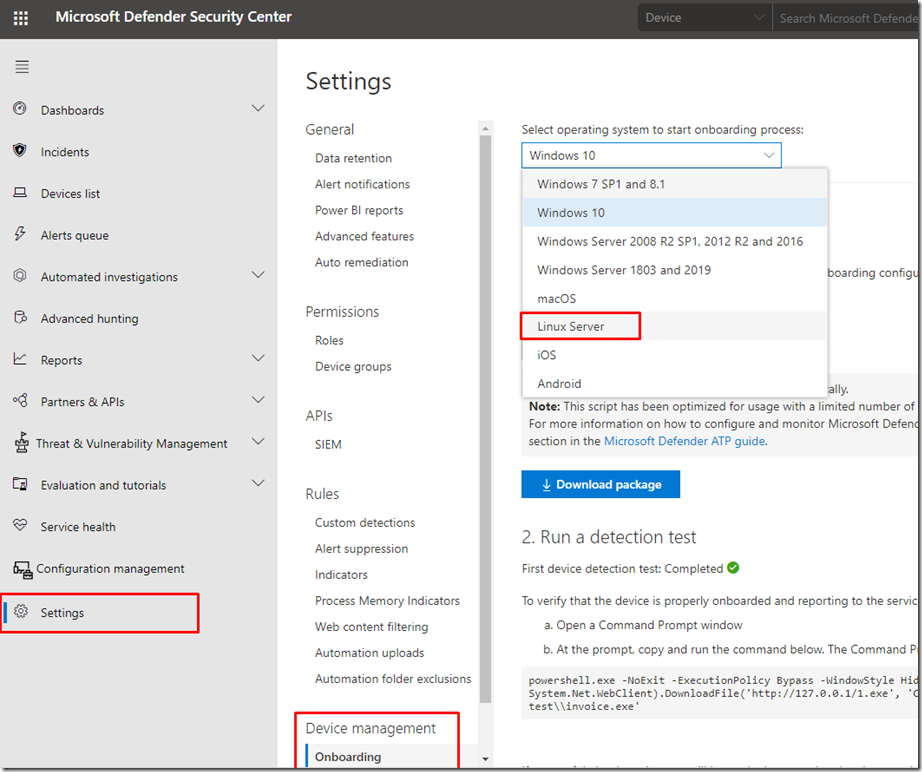
Configuration Steps – Part 2
7. On Exchange: Enable OWA VD Instant Messaging
8. On Exchange: Enable Messaging on OWA Policy
9. On Exchange: Create Enterprise Application for Skype Pool.
10. On Exchange: Create new SettingOverride for Skype for Business.
11- Generate a new Certificate for Exchange IM
12. Assign the newly imported certificate to IIS Exchange Back End site
13. On Exchange: Restart the WebAppPool
14. Log out and sign back in to OWA to Check
15. Troubleshooting methods
7- On Exchange Server: Enable OWA VD Instant Messaging
Part of enabling IM integration between Exchange and SfB is to enable OWA Virtual Directory to allow this. The below cmdlet does the job for you on all your Exchange Servers
From Exchange, Launch Exchange Management and run the following cmdlet
Get-OwaVirtualDirectory | Set-OwaVirtualDirectory -InstantMessagingEnabled $true -InstantMessagingType Ocs
![clip_image001[6]_thumb clip_image001[6]_thumb](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0016_thumb_thumb.png)
8- On Exchange: Enable Messaging on OWA Policy
Run the following to enable Messaging for Owa Policy
Get-OwaMailboxPolicy | Set-OwaMailboxPolicy -InstantMessagingEnabled $true -InstantMessagingType Ocs
![clip_image001[6]_thumb[1] clip_image001[6]_thumb[1]](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0016_thumb1_thumb.png)
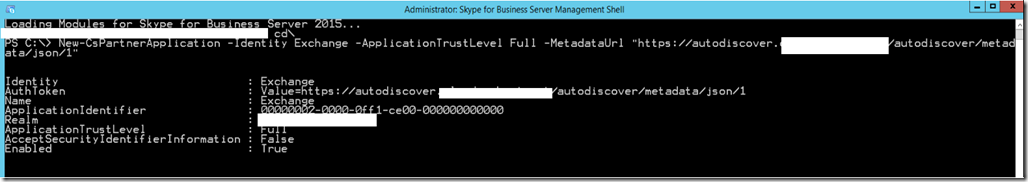
9- On Exchange: Create Enterprise Application for Skype Pool.
From Exchange Management shell Run the following cmdlet
Cd $exscripts
.\Configure-EnterprisePartnerApplication.ps1 -AuthMetadataUrl “https://sbg-pool01.domain.com/metadata/json/1” -ApplicationType Lync
The AuthMetadataUrl is going to be your local Skype for Business Pool URL. This URL should work in your Exchange server without any Certificate error. Meaning that the certificate assigned to your Skype for Business pool should already be imported to Exchange Servers to trust this URL.
![image_thumb[14] image_thumb[14]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb14_thumb.png)
If your previous configuration is correct then you should see the “The Configuration has Succeeded” Message.
10- On Exchange: Create new SettingOverride for Skype for Business.
Notes:
New-SettingOverride -Name “<UniqueOverrideName>” -Component OwaServer -Section IMSettings -Parameters @(“IMServerName=<Skype server/pool name>”,”IMCertificateThumbprint=<Certificate Thumbprint>”) -Reason “<DescriptiveReason>” [-Server <ServerName>]
The Thumbprint you use here will define if whether IM will work or not as this what secures the communication between Exchange and Skype. If you use the wrong certificate your Integration will fail and users wont be able to login to IM through OWA.
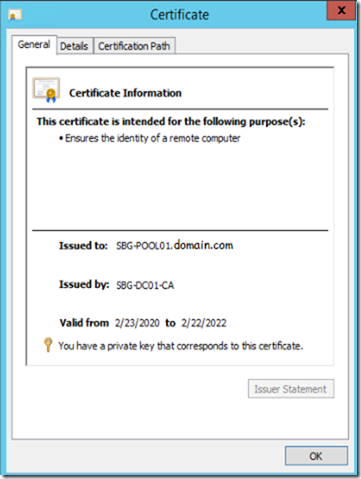
11- Generate a new Certificate for Exchange IM
IMPORTANT NOTE:
In order for IM in OWA to work the certificate you will generate must have its common name set as mail.domain.com to match the configuration.
Using Digicert tool on Exchange Server I will generate the CSR of the new certificate
Click on Create CSR
![image_thumb[15] image_thumb[15]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb15_thumb.png)
Choose SSL certificate type and make sure you choose Mail.domain.com as CN
In the SANs type all of the involved servers (Skype for Business Frontends, Mailbox servers in FQDN and in Hostnames as in the screenshot below). and click on Generate
![image_thumb[16] image_thumb[16]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb16_thumb.png)
- Go to your CA Server’s CertSRV URL and copy the CSR code there to generate the new certificate.
- Import the new certificate to the current server, then export it in PFX format and import it to all the Exchange Servers you’re planning to use.
![image_thumb[18] image_thumb[18]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb18_thumb.png)
- After importing the certificate I will verify that I can see the private key
![image_thumb[19] image_thumb[19]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb19_thumb.png)
Click on the Details and copy the Thumbprint or from MMC right click the certificate > Properties give it a friendly name e.g. (IM) and then from Exchange Management shell you can copy the Thumbprint directly.
Get-ExchangeCertificate | select thumbprint,friendlyName
![image_thumb[20] image_thumb[20]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb20_thumb.png)
Now use the previous script to create the setting Override for OwaServer.
Things you can change are in bold “Name, IM Servername Value, and the Thumbprint value”.
New-SettingOverride -Name “IM Override” -Component OwaServer -Section IMSettings -Parameters @(“IMServerName=SBG-Pool01.domain.com“,”IMCertificateThumbprint= 28E4B1BA0F2FCB1535AF199F02A64EFC78367F2D“) -Reason “Configure IM”
![image_thumb[21] image_thumb[21]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb21_thumb.png)
If you enter the server parameter to use a single server you can change that by using. Note that you must not use FQDN but rather only the server’s hostname.
Get-SettingOverride | Set-SettingOverride -Server sbg-mx01,sbg-mx02
![image_thumb[22] image_thumb[22]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb22_thumb.png)
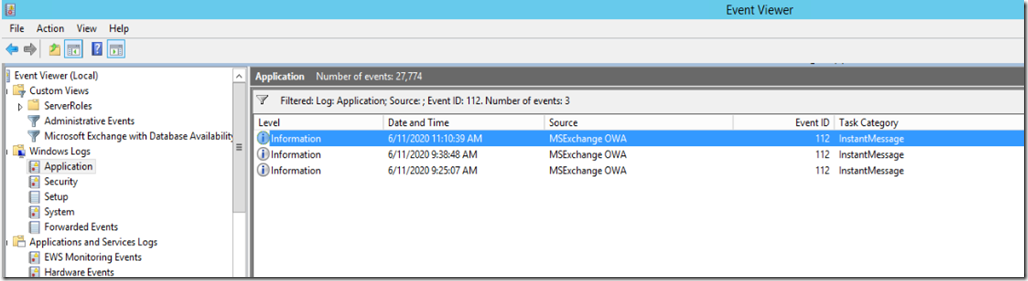
This should generate an event ID 112 on Exchange servers involved in the deployment.
![clip_image001[9]_thumb clip_image001[9]_thumb](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0019_thumb_thumb.png)
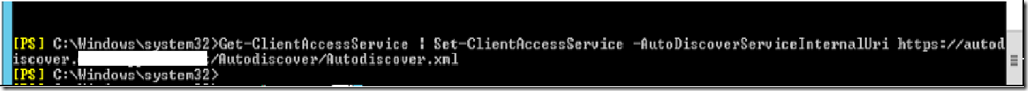
12. Assign the newly imported certificate to IIS Exchange Back End site
Once the certificate is in the server store, You will be able to easily find in from IIS and bind it to the Exchange Back End site.
This is the most crucial step to get IM to work in OWA. Don’t worry about breaking up Exchange Sites or Powershell. If you have added Exchange Servers Hostnames and FQDNs in this certificate then you should be good.
- Now Launch IIS
- Click on Exchange Back End
- Select Binding
- Click on the 444 port and edit
- Select the newly generated certificate that has the mail.domain.com as CN. (This certificate must also have all Exchange Servers hostnames and FQDNs set as SANs)
![image_thumb[23] image_thumb[23]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb23_thumb.png)
![image_thumb[24] image_thumb[24]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb24_thumb.png)
Make sure you change the backend cert to the new on all the involved Exchange Servers.
13. On Exchange: Restart the WebAppPool
Restart-WebAppPool MSExchangeOWAAppPool
![image_thumb[25] image_thumb[25]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb25_thumb.png)
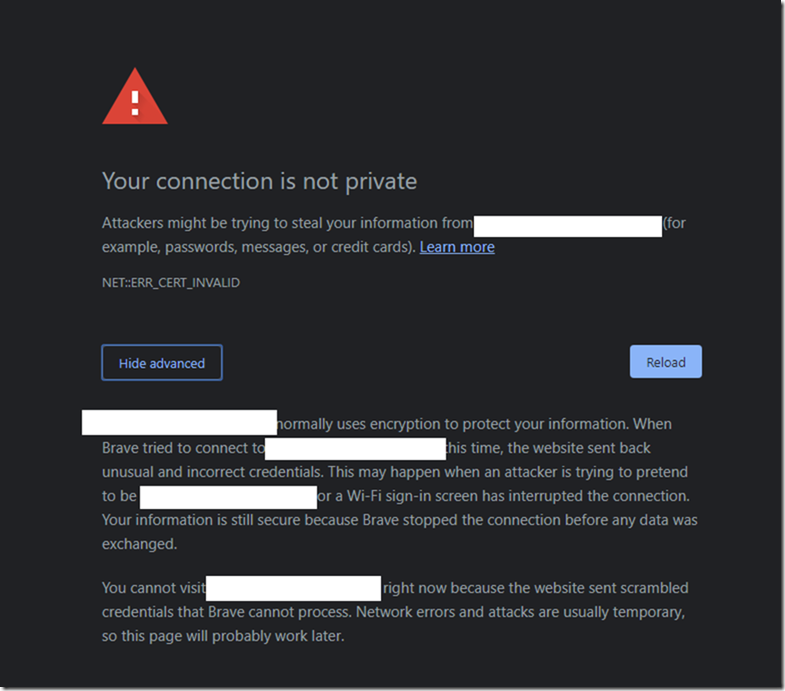
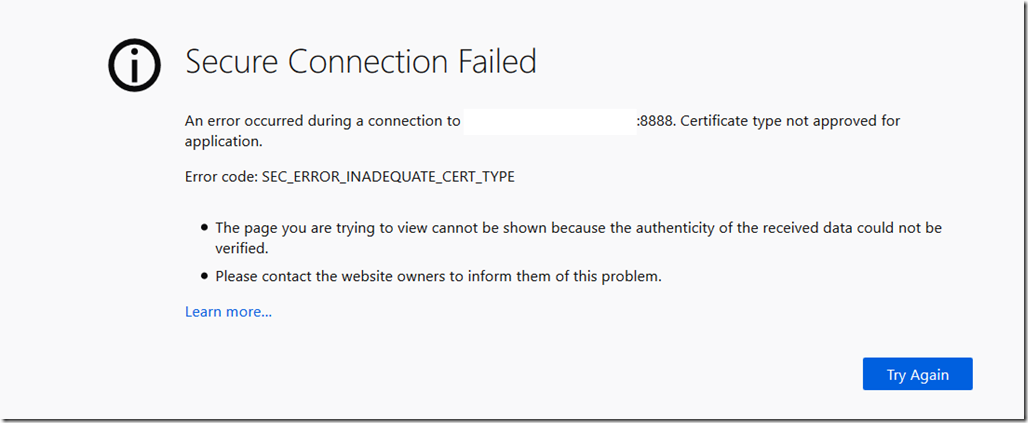
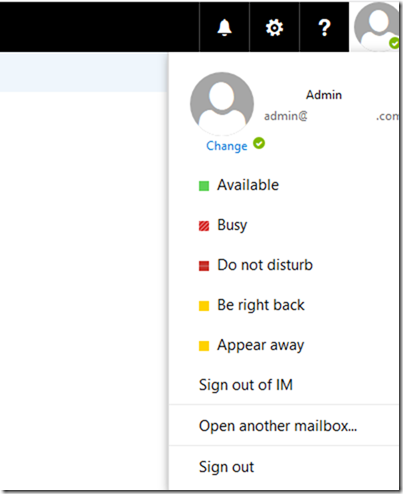
14. Log out and sign back in to OWA to Check
Log out of OWA and back in and check if you are able to Login to IM . It should normally sign you in automatically but in case of an error then you should see it.
![image_thumb[29] image_thumb[29]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb29_thumb.png)
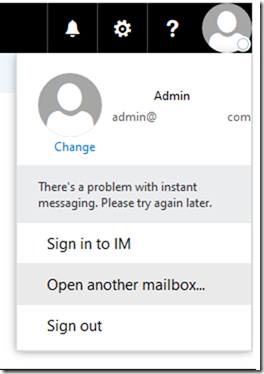
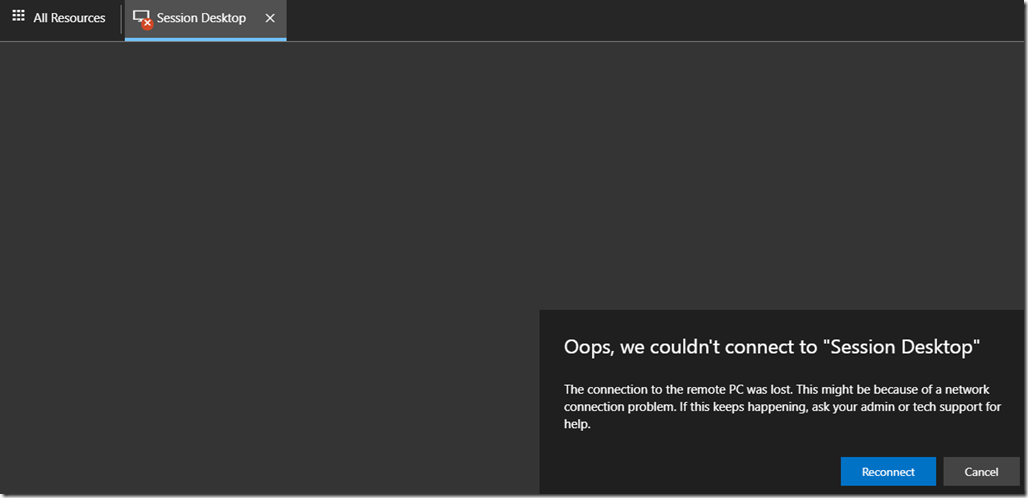
In case of an error you should see the following.
![image_thumb[27] image_thumb[27]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb27_thumb.png)
If it works then you should see the presence
![image_thumb[28] image_thumb[28]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb28_thumb.png)
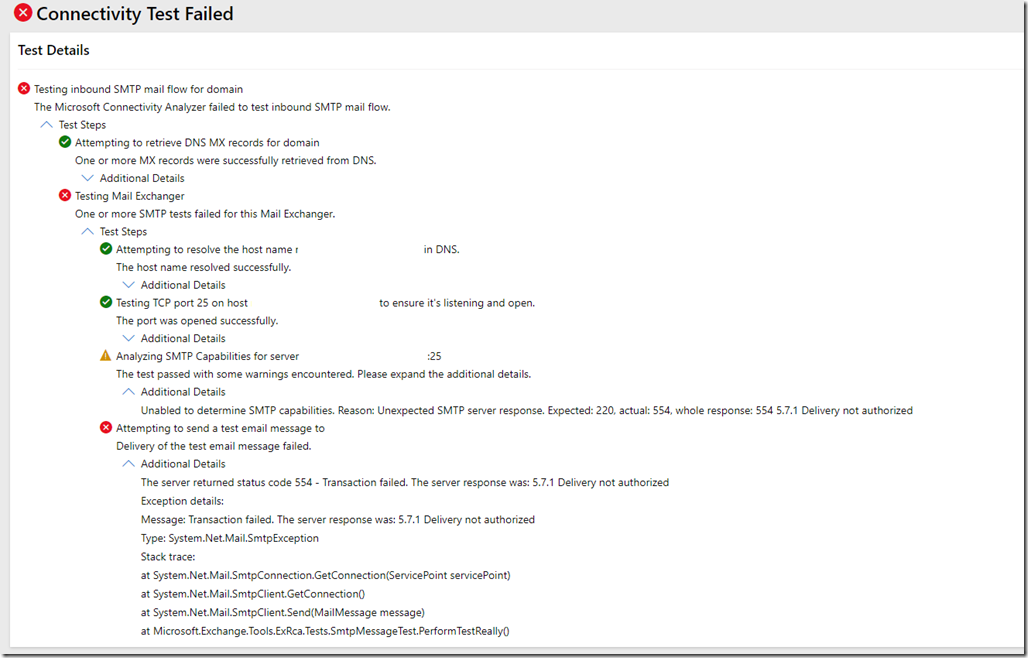
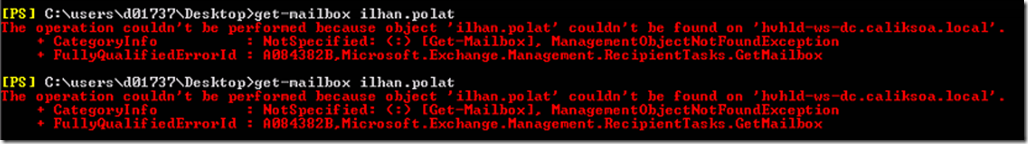
15. Troubleshooting Methods
If you follow the above steps correctly then it should work especially when applying the right certificate for your Exchange Back End IIS part however if you face an error then you should do the following steps to troubleshoot the error
- Set the Eventlog for Instant Messaging on Exchange from Low to High
Set-EventLogLevel -Identity “sbg-mx01\MSExchange OWA\InstantMessage” -Level High
![image_thumb[30] image_thumb[30]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb30_thumb.png)
- Look in the following path for errors
C:\Program Files\Microsoft\Exchange Server\V15\Logging\OWA\InstantMessaging
- Check the Healthset of the OWA Instant Messaging.
Get-ServerHealth -HealthSet OWA.Protocol.Dep -Server sbg-mx01 | Format-Table Name, AlertValue –Auto
![image_thumb[31] image_thumb[31]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb31_thumb.png)
Get-MonitoringItemIdentity -Server sbg-mx01 -Identity OWA.Protocol.Dep | Format-Table Identity,ItemType,Name -Auto
![image_thumb[32] image_thumb[32]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb32_thumb.png)
Ref
https://docs.microsoft.com/en-us/exchange/plan-and-deploy/post-installation-tasks/configure-im-integration-with-owa?view=exchserver-2019
https://docs.microsoft.com/en-us/exchange/high-availability/managed-availability/health-sets?view=exchserver-2019
![clip_image001[6]_thumb clip_image001[6]_thumb](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0016_thumb_thumb.png)
![clip_image001[6]_thumb[1] clip_image001[6]_thumb[1]](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0016_thumb1_thumb.png)
![image_thumb[14] image_thumb[14]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb14_thumb.png)
![image_thumb[15] image_thumb[15]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb15_thumb.png)
![image_thumb[16] image_thumb[16]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb16_thumb.png)
![image_thumb[18] image_thumb[18]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb18_thumb.png)
![image_thumb[19] image_thumb[19]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb19_thumb.png)
![image_thumb[20] image_thumb[20]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb20_thumb.png)
![image_thumb[21] image_thumb[21]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb21_thumb.png)
![image_thumb[22] image_thumb[22]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb22_thumb.png)
![clip_image001[9]_thumb clip_image001[9]_thumb](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0019_thumb_thumb.png)
![image_thumb[23] image_thumb[23]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb23_thumb.png)
![image_thumb[24] image_thumb[24]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb24_thumb.png)
![image_thumb[29] image_thumb[29]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb29_thumb.png)
![image_thumb[27] image_thumb[27]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb27_thumb.png)
![image_thumb[28] image_thumb[28]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb28_thumb.png)
![image_thumb[31] image_thumb[31]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb31_thumb.png)
![image_thumb[32] image_thumb[32]](https://www.moh10ly.com/wp-content/uploads/2020/06/image_thumb32_thumb.png)



![clip_image001[4] clip_image001[4]](https://www.moh10ly.com/wp-content/uploads/2020/06/clip_image0014_thumb.png)
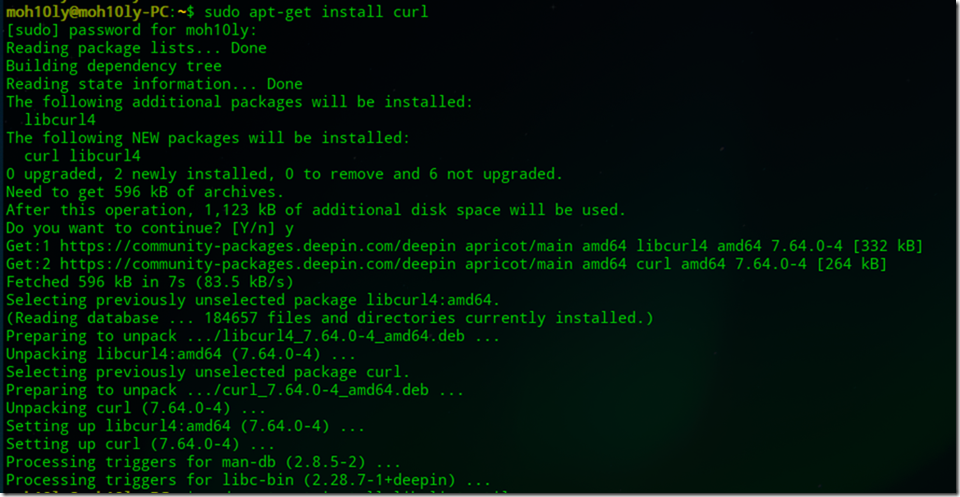
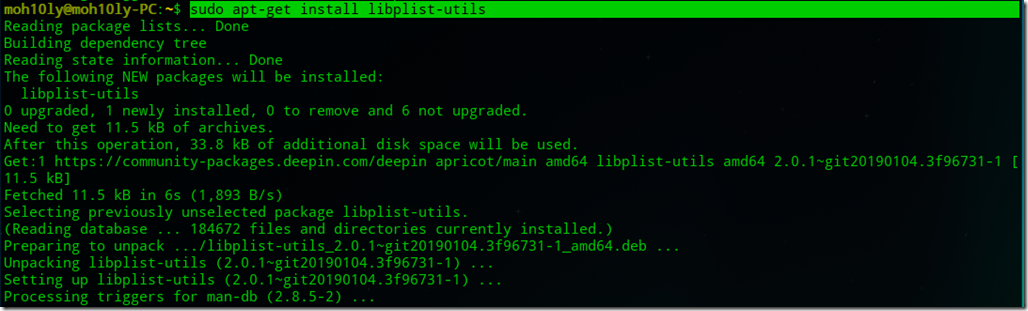
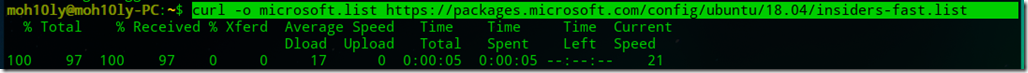
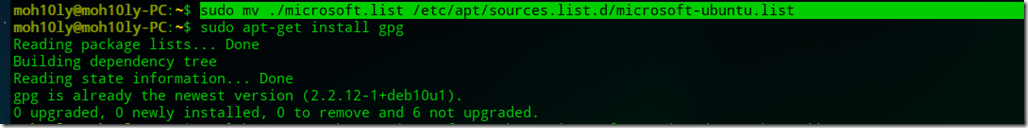
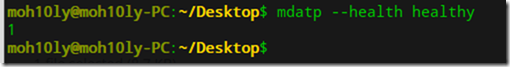
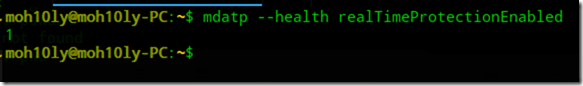
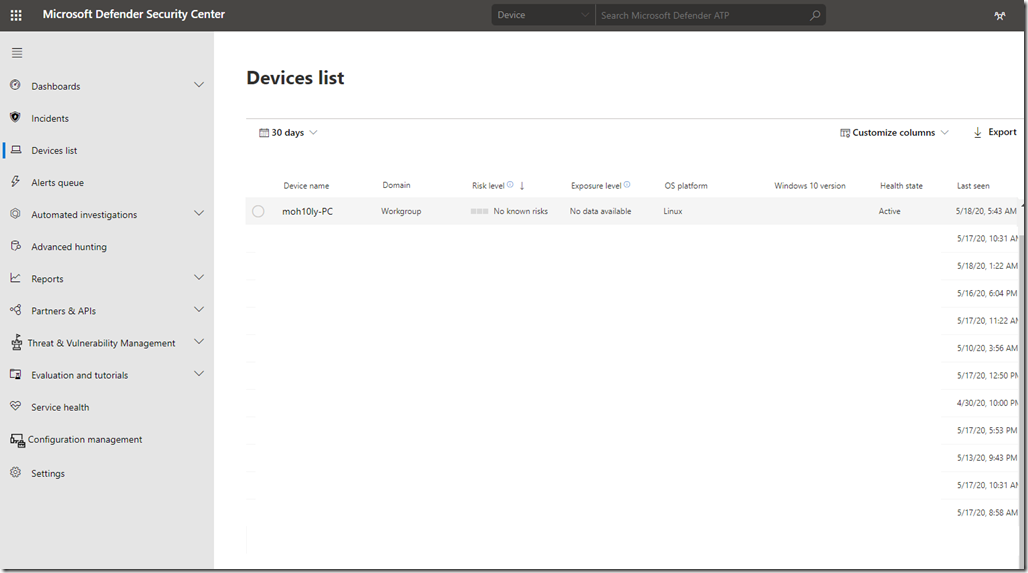
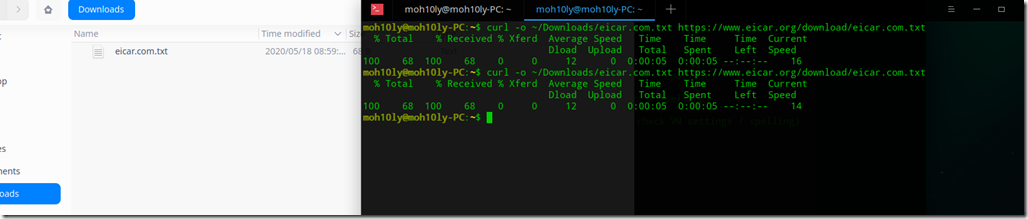
![clip_image001[4] clip_image001[4]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image0014_thumb.png)
![clip_image001[6] clip_image001[6]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image0016_thumb-2.png)
![clip_image001[6] clip_image001[6]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image0016_thumb-1.png)
![clip_image001[10] clip_image001[10]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image00110_thumb.png)
![clip_image001[8] clip_image001[8]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image0018_thumb.png)
![clip_image001[12] clip_image001[12]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image00112_thumb.png)
![clip_image001[14] clip_image001[14]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image00114_thumb.png)
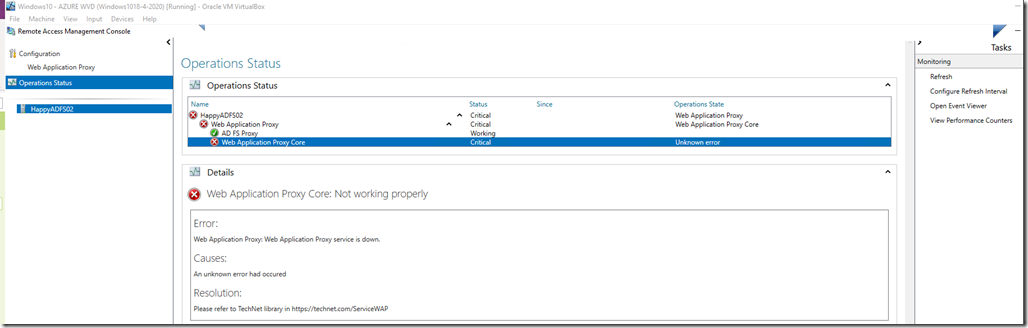
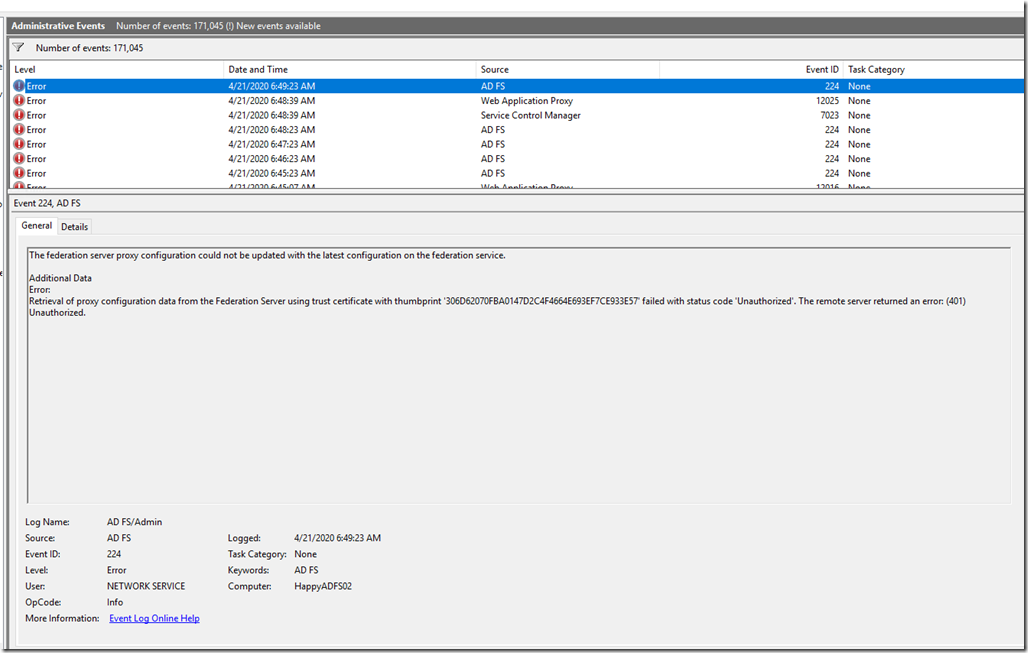
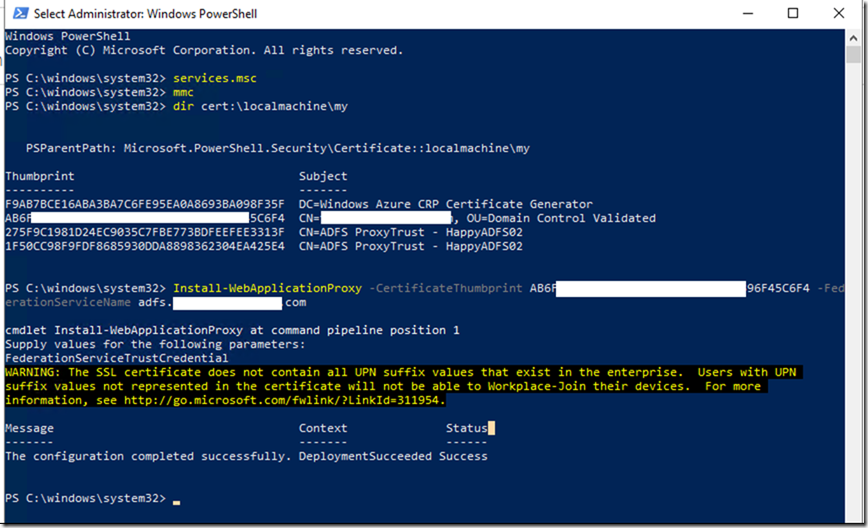
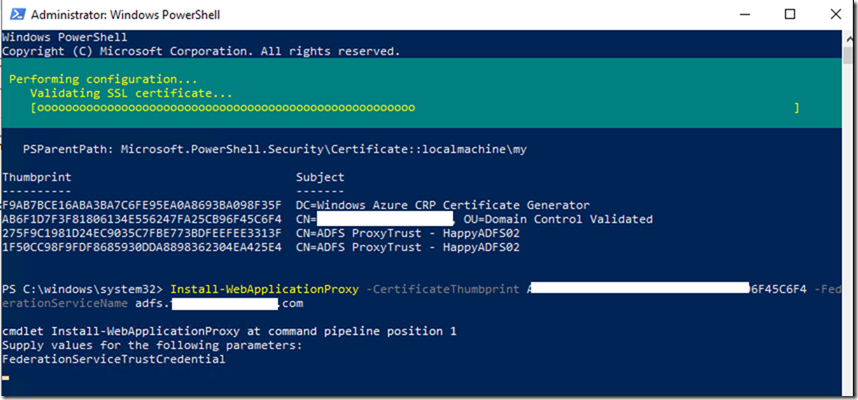
![clip_image001[6] clip_image001[6]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image0016_thumb.png)