The Story
after installing Zammad ticketing system I tried to implement Let’sEncrypt certificate to secure the system but there was nothing available on the internet except an old article about implementing this on Ubuntu 16 with Nginx (see article here).
In my case I was using apache and no Nginx in place, and after installing Zammad it was using pretty fine on Http but needed to redirect http to HTTPS after implementing the certificate.

Solution:
I first Installed Certbot for apache and then I took a backup of all my Zammad configuration and made sure not to alter the default Zammad directory.
So I created a dummy folder called /var/www/support and a file called /var/www/support/index.html within that folder and provided them the appropriate permissions.
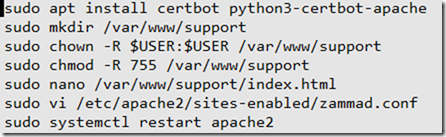
sudo apt install certbot python3-certbot-apache
sudo mkdir /var/www/support
sudo chown -R $USER:$USER /var/www/support
sudo chmod -R 755 /var/www/support
sudo nano /var/www/support/index.html
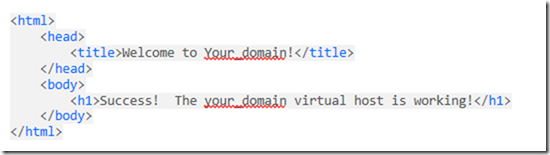
Edit the index.html file with the following to make sure that it works
<html>
<head>
<title>Welcome to Your_domain!</title>
</head>
<body>
<h1>Success! The your_domain virtual host is working!</h1>
</body>
</html>
Edit Zammad’s Default Config File
Please make sure you take a move the original copy of Zammad file to another location using the following command
sudo mv /etc/apache2/sites-enabled/zammad.conf /etc/apache2/sites-enabled/zammad.bak
Then we’ll replace the file with this configuration but since we moved the original file to .bak then we’ll have to recreate it with our intended configuration.
Edit a new zammad.conf file and copy the configuration below
sudo vi /etc/apache2/sites-enabled/zammad.conf
Configuration starts below this:
#
# this is the apache config for zammad
#
# security – prevent information disclosure about server version
#ServerTokens Prod
<VirtualHost *:8080> # I changed the default port of Zammad to 8080 to allow Letsencrypt to connect on 80 and create the certificate
# replace ‘localhost’ with your fqdn if you want to use zammad from remote
ServerName localhost:8080
## don’t loose time with IP address lookups
HostnameLookups Off
## needed for named virtual hosts
UseCanonicalName Off
## configures the footer on server-generated documents
ServerSignature Off
ProxyRequests Off
ProxyPreserveHost On
<Proxy 127.0.0.1:3000>
Require local
</Proxy>
ProxyPass /assets !
ProxyPass /favicon.ico !
ProxyPass /apple-touch-icon.png !
ProxyPass /robots.txt !
ProxyPass /ws ws://127.0.0.1:6042/
ProxyPass / http://127.0.0.1:3000/
— INSERT — 10,38 Top
DocumentRoot “/opt/zammad/public”
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<Directory “/opt/zammad/public”>
Options FollowSymLinks
Require all granted
</Directory>
</VirtualHost>
<VirtualHost *:80>
ServerName support.cloud-net.tech
DocumentRoot /var/www/support
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
– ————————-
In the above configuration we did two things:
1- Replacing the original Zammad listening port instead of 80 to 8080
2- Created a new virtual host that points to our dummy folder /var/www/support
Save the file and exit from vi
Make sure you restart Apache after this
sudo systemctl restart apache2
Enable the new site configuration
sudo a2ensite zammad.conf
Lets create the certificate
In the below commands , the first one will drive you through the process of getting the certificate.
The second checks the status of the configuration of the auto renewal script certbot and third command tests the renewal of the certificate.
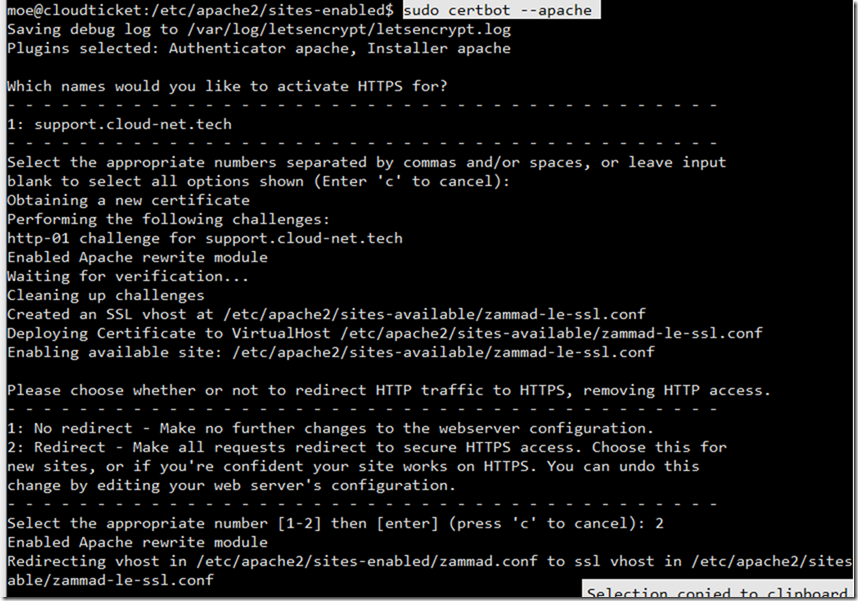
1- sudo certbot –apache
2- sudo systemctl status certbot.timer
3- sudo certbot renew –dry-run
As you can see in the below screenshot the command also asks you if you’d like to redirect all http traffic to HTTPS. You should want to say Y to that.
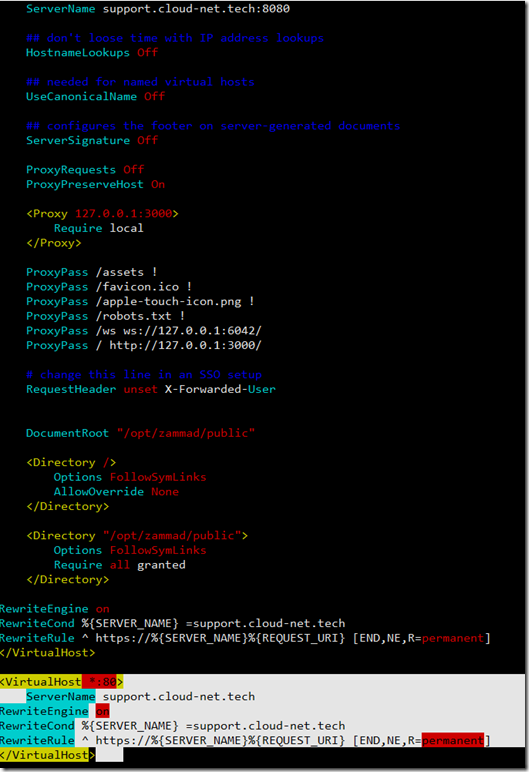
When you accept creating Redirection rule from HTTP to HTTPs the main Zammad config will get that configuration which wont work in that case because we already changed the default zammad port to 8080.
So you’ll need to get into that zammad.conf that you created again and enter the redirection portion
# this is the apache config for zammad
#
# security – prevent information disclosure about server version
#ServerTokens Prod
<VirtualHost *:8080>
# replace ‘localhost’ with your fqdn if you want to use zammad from remote
ServerName support.cloud-net.tech:8080
## don’t loose time with IP address lookups
HostnameLookups Off
## needed for named virtual hosts
UseCanonicalName Off
## configures the footer on server-generated documents
ServerSignature Off
ProxyRequests Off
ProxyPreserveHost On
<Proxy 127.0.0.1:3000>
Require local
</Proxy>
ProxyPass /assets !
ProxyPass /favicon.ico !
ProxyPass /apple-touch-icon.png !
ProxyPass /robots.txt !
ProxyPass /ws ws://127.0.0.1:6042/
ProxyPass / http://127.0.0.1:3000/
# change this line in an SSO setup
RequestHeader unset X-Forwarded-User
DocumentRoot “/opt/zammad/public”
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<Directory “/opt/zammad/public”>
Options FollowSymLinks
Require all granted
</Directory>
RewriteEngine on
RewriteCond %{SERVER_NAME} =support.cloud-net.tech
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]
<VirtualHost *:80>
ServerName support.cloud-net.tech
RewriteEngine on
RewriteCond %{SERVER_NAME} =support.cloud-net.tech
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]
</VirtualHost>
Note:
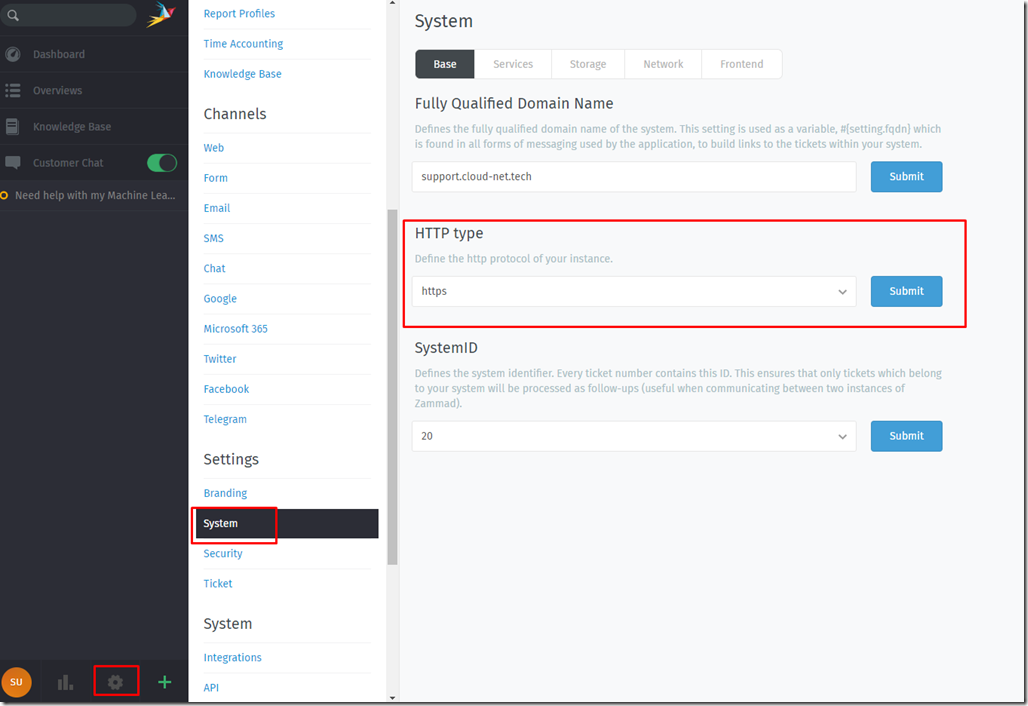
You need to make sure that you have enabled port 443 on your Firewall and changed the main protocol of Zammad to HTTPs
To do so you’ll need to get into the Zammad portal > Settings > System > Http Type and change that to HTTPS.
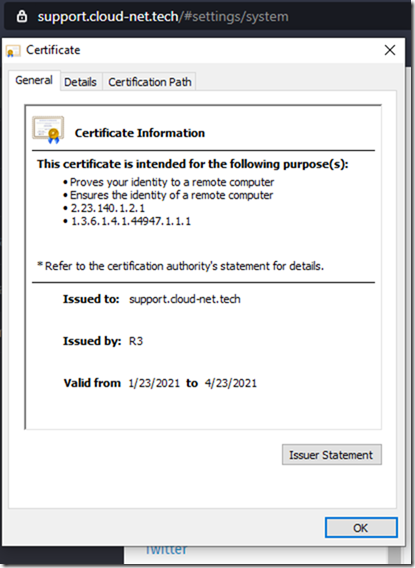
That’s it, my example here worked as expected and now my traffic is automatically getting redirected to https.
Hope this helps anyone looking for such configuration.
Please consider donating to this Bitcoin account if you like this article or website.
![clip_image001[4] clip_image001[4]](https://www.moh10ly.com/wp-content/uploads/2021/01/clip_image0014_thumb-1.png)